Changelog
Follow up on the latest improvements and updates.
RSS
Within relationship based access control policies, it's often interesting to get all the objects a user can access (which is already supported via permit.getUserPermissions()).
We now added the reverse functionality as well via a new SDK method:
permit.getAuthorizedUsers()
.With this new method, it's possible get all users who have access to a resource.
Check out the docs here: https://docs.permit.io/how-to/enforce-permissions/authorized-users
Example (python):
from permit import Permit, AuthorizedUsersResult
permit = Permit(...)
authorized_users: AuthorizedUsersResult = permit.authorized_users(
"read", "repo",
)
The schema of the response in the code above is as follows:
{
"resource": "repo:*",
"tenant": "default",
"users": {
"user1": [
{
"user": "user1",
"tenant": "default",
"resource": "__tenant:default",
"role": "admin"
}
]
}
}
Permit.io offers a unique UI condition builder to build complex attribute based access policies. We now added new types of attributes and operators to support more advanced use cases.
The
Object
typed attribute allows an attribute to contain multiple sub attributes at once, and the Array<Object>
(object array) typed attributes allows an attribute to contain a list of dictionary (object) attributes.Check out the docs here: https://docs.permit.io/api/working-with-abac/operators#object-match-operators
new
Permit Elements 🧠
Access Requests Element
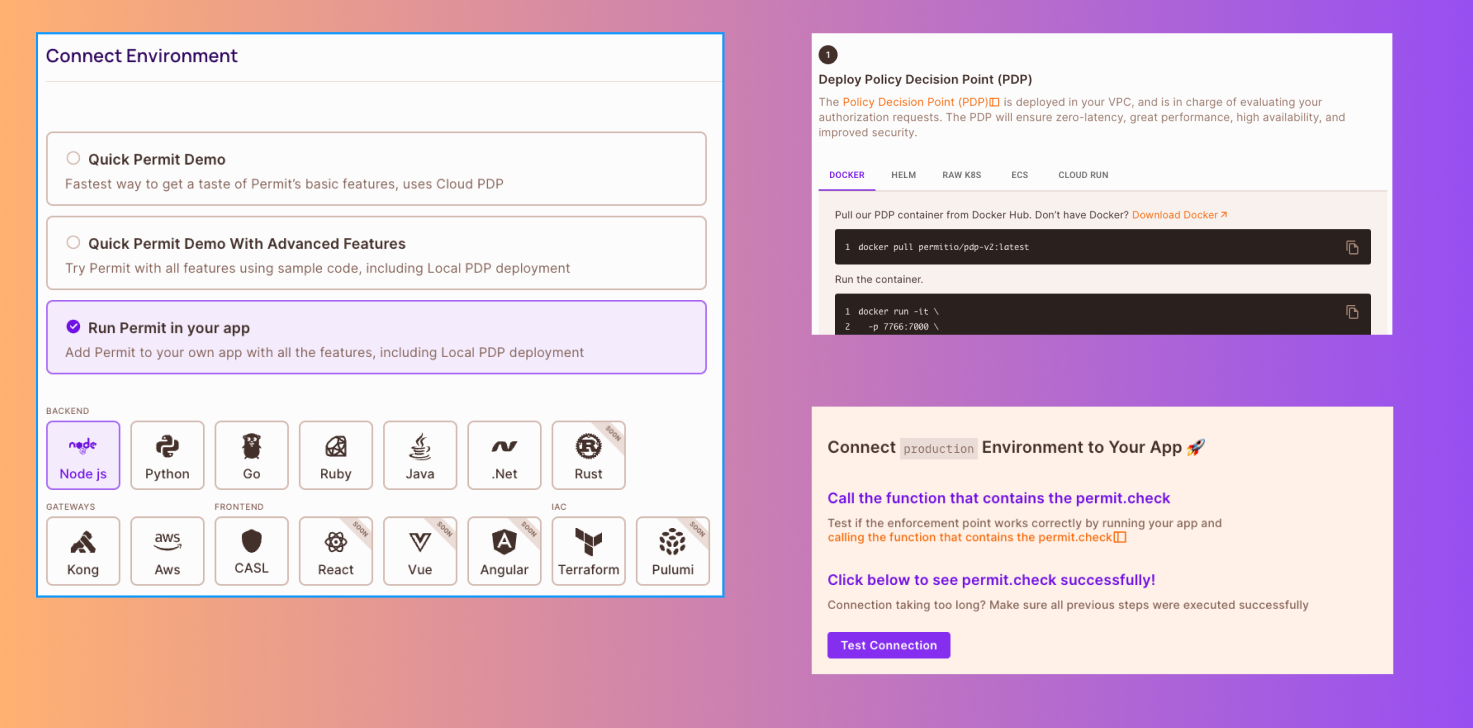
The Access requests features is now available via a Permit Element.
You can embed a fully functional UI in your app that allows users to request access from other users who can then approve or deny the request. If approved, the user will be granted new permissions.
Check out the docs here: https://docs.permit.io/embeddable-uis/element/access-request
The new Access Request API allows to create access requests for specific roles or resource instances. It also assigns relevant moderators to approve or deny user requests based on your decision.
With this new API, an end-user without permissions can ask the relevant permissions from a different end-user.
Check out the docs here: https://docs.permit.io/api/examples/access-requests
improved
Simplified onboarding experience
We have just shipped a new onboarding experience for new customers that we hope will enable users to adopt modern authorization with a few less clicks.
It's now easier than ever to start using Permit.io.
Create your account
Start a new workspace
And follow the instructions :)
Check out the Getting Started docs.
new
Policy Improvements 🧪
Integrations 🔗
GetUserPermissions()
To get all user permissions irrespective of the tenant, you can use the
permit.getUserPermissions()
function. This function determines all user permissions for every registered resource across all tenants, and allows you to get all the objects (resource instances) the user can access in a single API call.Example usage:
const { Permit } = require("permitio");
const permit = new Permit({token: "<YOUR_API_KEY>", ...});
const userPermissions = await permit.getUserPermissions("john@doe.com");
Example output:
{
"result": {
"__tenant:default": {
"permissions": [
"document:read",
"task:read"
],
"roles": [
"viewer"
],
"tenant": {
"attributes": {},
"key": "default",
"type": "__tenant"
}
},
"document:budget": {
"permissions": [
"document:read",
"document:update",
"document:delete"
],
"roles": [
"owner"
],
"resource": {
"attributes": {"finance": true},
"key": "budget",
"type": "document"
}
}
}
}
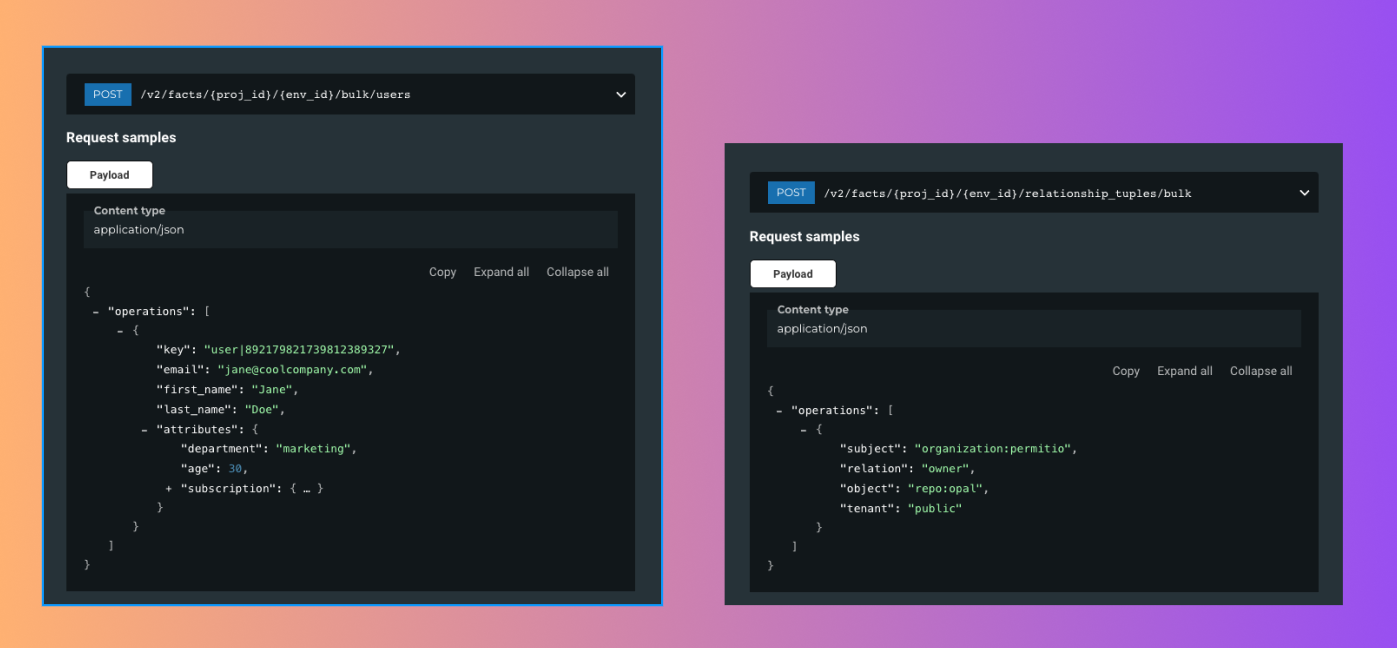
Permit.io API includes bulk APIs for selected operations, which offers a significant performance gains when trying to upload or change a lot of data at once.
The supported methods are:
- Bulk assign/unassign roles
- Bulk create/delete users
- Bulk create/delete tenants
- Bulk create/delete resource instances
- Bulk create/delete relationship tuples
new
Integrations 🔗
Bulk permission checks 🚀
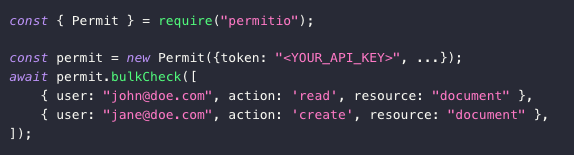
We added new types of permissions checks to our SDKs to allow you to perform many checks at once (bulkCheck) or check access across all tenants (checkInAllTenants).
Bulk Check
For some use cases, you might need to perform multiple
check()
calls at once. To support that, Permit provides a bulkCheck
function that allows you to validate multiple permission requests in a single call. In its basic form, the bulkCheck()
function accepts the same input parameters as the check()
function, but in an array.Check in All Tenants
To validate permissions irrespective of the tenant, you can use the
permit.checkInAllTenants
function. This function determines if a user has permissions for a specified action on a resource across all tenants, the response will be a list of tenants in which the user is allowed to perform the request.new
Permit Elements 🧠
New Features 🚀
User Management element now supports Resource Roles (ReBAC)
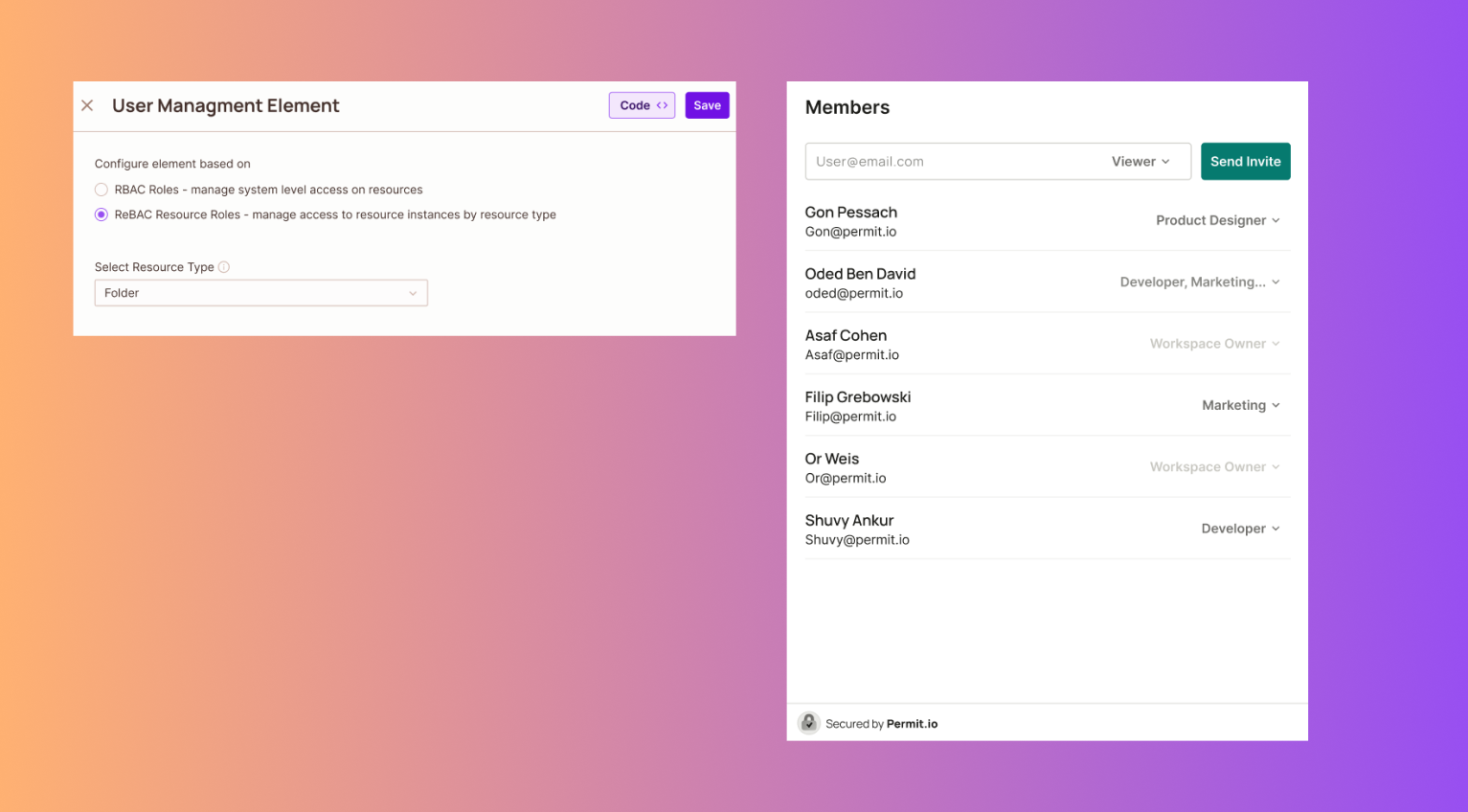
The User Management Element now allows you to manage access at a more granular level, allowing you to specify permissions for individual resource instances based on their type.
To learn how to embed this kind of elements, read the docs here.
Load More
→